Privacy Concerns Of Stripe Connect: Can The Developer Of Your WordPress Ecommerce Plugin See Your Store’s Transactions?
When you hit that button to connect your self-hosted WordPress store to Stripe, are you unknowingly exposing your transactions to a third party? I was skeptical, so I researched it myself. Here’s what I found.
Many site owners who use self-hosted shopping carts (like WooCommerce or FluentCart) think that one of the perks of that setup is privacy. But, what if the developer of that shopping cart software actually had the ability to view all of your store’s transactions, customers, withdrawals and more?
Could they “spy” on your business?
This was one of the contentions I first came across back when Easy Digital Downloads was acquired by Awesome Motive. I saw rumblings about the potential privacy problems of a lot of WordPress plugin developers who used EDD to sell their software suddenly concerned that Awesome Motive had backdoor access to all of their sales data. And obviously, Awesome Motive is competitor to most of these businesses so that would be of utmost concern. Here’s what Carl Hancock (founder of Gravity Forms) said at the time:
When the issue first arose, I couldn’t help wonder… is it true?
When you self-host your own store and use Stripe Connect to connect your store to your Stripe account, are you providing access to the plugin’s developer to see all of the internal activity of your store?
What Is Stripe Connect?
Stripe is, by far, the most popular platform for processing credit card orders on your website. It is a well-developed and well-known platform and it just works.
There are two ways that you can connect your store to your Stripe account. They are:
- Manually copy/paste your API keys. It will contain both a publishable (public) key and a secret key. You copy those API keys into your plugin and you’ll be connected.
- Using Stripe Connect. This method uses OAuth to connect to your Stripe account without the need to copy/paste keys. You click a button, log into your account, accept the permissions… and you’re done.
Stripe prefers and recommends the use of Stripe Connect. It is technically a more secure approach because it avoids the storage of both of your keys on your website. Indeed the Stripe Verified Partner program (a certification program for businesses that integrate with Stripe) requires the use of Stripe Connect.
Stripe Connect is also much more user-friendly. For instance, when you click to connect your WooCommerce store to Stripe using the official Stripe plugin, you get this:

Click the button and you’re on your way. But, what you see next is where the potential issue is…
Stripe Connect Permissions
When you get to the next screen, you get the following:
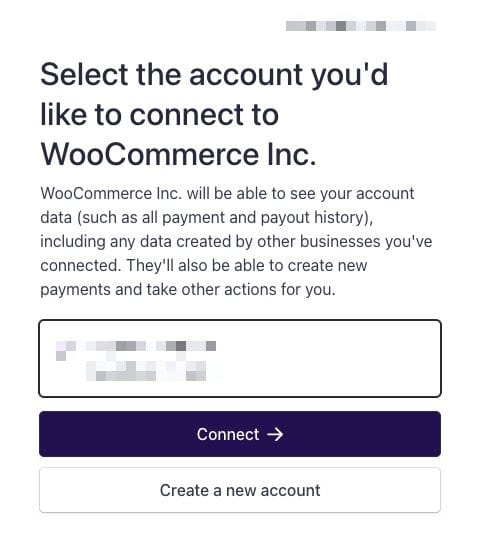
This is not WooCommerce specific. It is standard verbiage. Here’s when you go to connect FluentCart to Stripe:
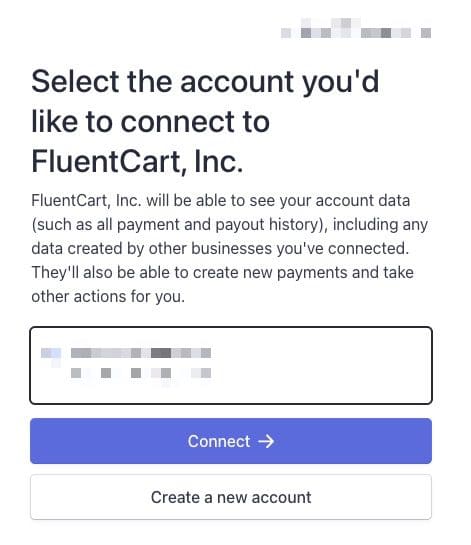
As it says…
[Developer Company] will be able to see your account data (such as all payment and payout history), including any data created by other businesses you’ve connected. They’ll also be able to create new payments and take other actions for you.
So, that’s interesting. It isn’t saying we’re sharing data with the plugin. It says we’re sharing it with the company.
So, what exactly does this mean? What exactly can they see?
Data That Vendors Have Access To
It was the founder of one of the leading ecommerce platforms for WordPress that brought this to my attention originally. My initial instinct, frankly, was to doubt what he was saying. For one, it seemed like a big security hole that Stripe would have a big problem with. Secondly, he was a competitor and I frankly felt he may have a vested interest in saying it.
I did some research on my own as well. After all, I am not the developer of a shopping cart and I have no Stripe Connect account or Stripe partnership. So, I have no direct way to know what vendors can and cannot see. But, this particular founder said to me:
David, I’m telling you, I could log in and see everyone connected to ****** or my WooCommerce payment gateway and view every single detail in all of their accounts if I chose to. And all those other e-commerce tools can do the same thing as well. I can see everything.
He went on to say:
Now, I can’t get credit card details, but I can see what payment method someone used to make a purchase as well. And I believe the last four digits, but I’m not sure about that. So payment data is secure, but you do get access to the customer’s name, customer’s email, everything that you have access to view. Any e-commerce tool that uses Stripe Connect, when someone clicks on that Connect button, their account is now connected to the e-commerce tool’s Stripe Connect account, and they can view all the details.
This doesn’t seem like common knowledge. Most people don’t know this. Frankly, I didn’t and I was skeptical. And from what I am told, most developers are quite happy with you not knowing that this is the case.
To be clear, this isn’t some juicy bit for plugin developers. Stripe literally gives them no choice. Stripe offers no other option for Stripe Connect that doesn’t show this data. While Stripe actively encourages all developers (even for self-hosted plugins) to use Stripe Connect for security reasons, it also means that even developers who have no need or desire to see that data DO have access to it – whether they want it or not.
How It Works, Direct From Stripe
The documentation for this is public in the Stripe documentation. For a vendor to use Stripe Connect, they have what is called a Platform account. Anybody who then uses Stripe Connect via that vendor’s software will then have a “connected account” to the platform account.
That platform account holder then has certain, limited access to the data in those connected accounts. This page about the Connect Overview page even shows what the inside of the account would look like:
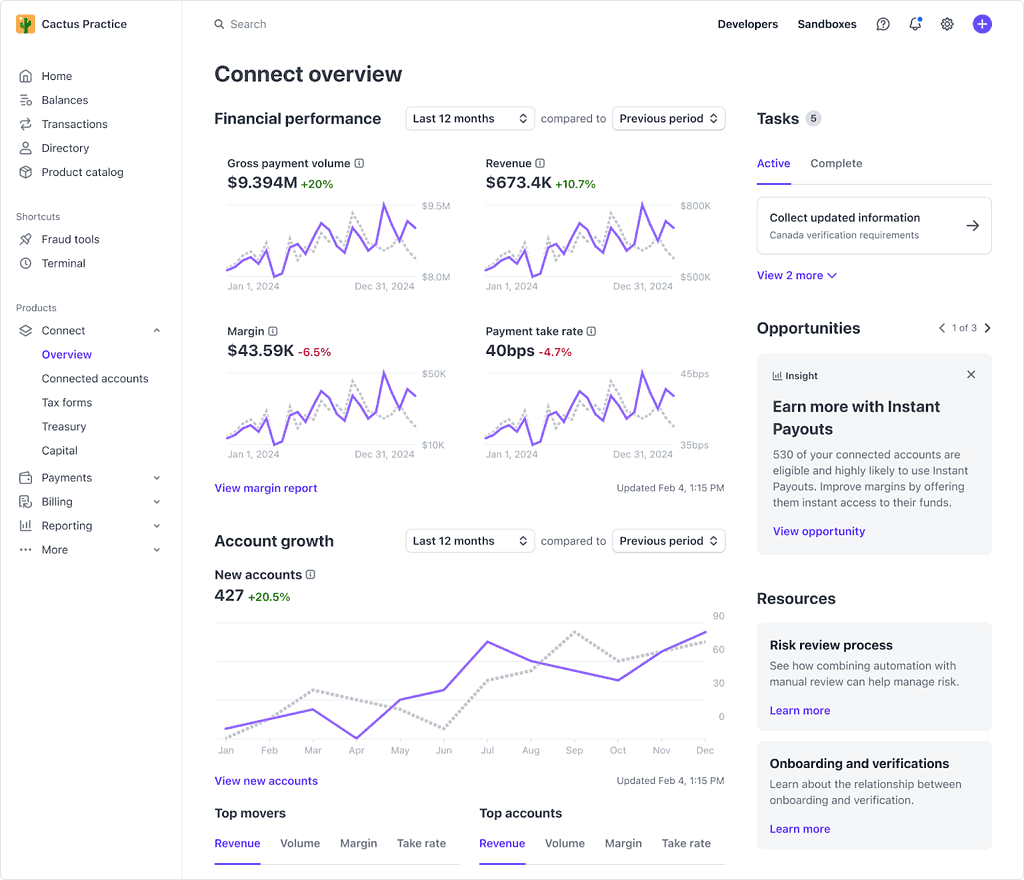
As you can see in the screenshot, there is an overview of the revenue from all connected accounts. Now it makes more sense when you see a plugin developer say things like how much revenue their plugin has handled. 😉
According to this document, the owner of the platform account can then view all connected accounts. For each, they can see the name of the account, pending payment balance and sales volume. The platform account owner can even “View As” for any connected account, basically viewing your Stripe account. This document shows the exact permissions provided. Not everything is viewable to them and there are some limits in place, however it is definitely not nothing. 🙂
Is This A Bad Thing?
Depends on your situation and your particular concerns. But, it is definitely something to be aware of.
The usage of Stripe Connect is actually a more secure way to connect to Stripe. It alleviates the storage of API keys directly on your WordPress install.
It is also useful for support purposes. The developers of these platforms (whether a self-hosted plugin or a SaaS platform) are able to provide better support and see what happened in transactions.
However, if you had the expectation of total privacy by self-hosting your own store, you could be disappointed. In the end, a self-hosted platform is only private if you don’t connect it to any outside sources at all. Obviously, connecting to a payment processor DOES mean that you’re sending customer data and transaction details to an external third-party by the very nature of the service. Stripe literally couldn’t process the order otherwise.
Stripe Platform accounts were primarily built for SaaS applications and marketplaces. It was designed for cases where a service provider is providing tools to a number of clients. It is helpful for support purposes and ease (and security) of connections. Frankly, it also enables options for additional transaction/merchant fees and the like. For instance, SureCart (a SaaS ecommerce platform) charges a 1.9% additional transaction fee for people without paid accounts. They can do this because of the Stripe Platform account.
Now, when it comes to WordPress plugins, these are not SaaS applications. They are self-hosted. But, most plugins that connect to Stripe also use Stripe Connect. They do this for simplicity for the end user and because, essentially, Stripe requires them to. But, this also means that you are a connected account for them in the world of Stripe. Some self-hosted stores may have ways to bypass Stripe Connect and connect directly via API, but that is something to consider beforehand (more on that later).
In the end, this is not a bad thing. It’s life. However, if you are worried about a potential competitor having access to your sales information, then this is something you want to be aware of.
I’ve personally never heard of instances of abuse of this. Stripe does indeed have limitations in place to protect certain capabilities for connected accounts. But, you definitely don’t have total privacy. In fact, the moment you connect your self-hosted store to a payment processor of any kind, you’re sending that data elsewhere.
Does This Present Legal Considerations (Like GDPR)?
When you are processing orders online, you are going to be sharing customer information with a third-party by nature. That third-party is, in this case, Stripe. You are the data controller and Stripe is the data processor.
The issue is that, if you’re using Stripe Connect, you’ve introduced a third actor – the platform. If you’re using a SaaS platform, then they are that third actor. However, even if you’re using a self-hosted WordPress shopping cart, you’d be using that company as the platform and they become the third party with access to customer information. Now, you have the data controller (you), the data processor (Stripe), and a third-party processor (the plugin developer).
So, yes, you need to account for the role of the platform (the plugin developer) in your site’s privacy policy and data disclosures.
When it comes to data processing agreements and the legals, Stripe has a built-in agreement to cover their role as the data processor. Stripe also has strict policies for Platform account holders and my understanding is that they even do audits on the matter. So, at least in terms of Stripe, things are kosher.
Things are a little more muddy when it comes to plugin developers, however. While everything is kosher, the mere fact that they COULD look at customer data makes them another data controller. Especially in the case of European site owners where GDPR compliance is way more stringent, this is something that must be accounted for. You would want to verify with the plugin developer their own policies in this regard and be sure you mention them in your own privacy policy.
How To Avoid This
In my opinion, Stripe should provide a Stripe Connect option for developers that doesn’t expose connected accounts. Their current design offers no differentiation between a SaaS marketplace and a self-hosted piece of software. My understanding is that this feature has been requested of Stripe before, but they have not delivered.
Not having this option puts developers in a weird position. They’re actively encouraged by Stripe to use Stripe Connect. It is actually required to be in the Verified Partner program. It IS a more secure way to connect to Stripe. Yet, it puts developers of self-hosted software into this position.
The only way to avoid it is not to use Stripe Connect and instead connect to Stripe using your own API keys. By doing it this way, the communication will be solely between your self-hosted WordPress site and your own Stripe account. There will be no other parties involved.
Thing is, this presents a new set of issues.
First off, not all WordPress plugin gateways to Stripe actually enable direct usage of API keys. The official Stripe plugin for WooCommerce doesn’t provide this option any longer and they deprecated manual entry of API keys. In fact, WooCommerce is actually requiring the new setup as of October 20, 2025. Seemingly most Stripe gateway plugins for WordPress require usage of Stripe Connect. In fact, Stripe even has a page about “Legacy Plugins” that directly states:
The plugin integration pattern is deprecated. This means you can no longer request secret API keys from users. Stripe Apps is the new method for authenticating users and includes support for both restricted API keys and OAuth 2.0. For more information, see the migration docs.
Also…
Previously, Stripe allowed plugins to request the standard API keys of a user to integrate with their products. As of September 30, 2024, Stripe requires all plugin developers to adopt secure authentication methods (restricted API Key, OAuth 2.0, or Stripe Connect) to protect users against fraud. All existing and new plugin developers must use one of these secure authorization methods. Migrating your plugin to an OAuth 2.0 app meets this requirement.
Some software still have backdoor methods to use your own API keys. The idea is that for self-hosted stores, you still have the right to do that. For instance, FluentCart provides the option to put your Stripe keys into wp-config.php like so:
define('FCT_STRIPE_LIVE_PUBLIC_KEY', 'YOUR_KEY_HERE');
define('FCT_STRIPE_LIVE_SECRET_KEY', 'YOUR_KEY_HERE');
define('FCT_STRIPE_TEST_PUBLIC_KEY', 'YOUR_KEY_HERE');
define('FCT_STRIPE_TEST_SECRET_KEY', 'YOUR_KEY_HERE');Now, any self-hosted plugin that provides the option to directly enter your API keys, you definitely DO need to consider the security of that.
Avoiding Security Issues Of Directly Entering Your API Keys
Even though it is getting harder to find Stripe plugins and carts that enable direct entry of your own API keys, they are still out there. But, this is definitely a case where you’re potentially replacing one issue with a much larger one.
Simply put, if a bad actor managed to get ahold of your Stripe API keys, they could cause all kinds of financial damage via your Stripe account. Consider the case of Shannon Mattern who had her Stripe account hacked and she was out $70,000. It is quite the story that you can read here.
The issue is that storing these keys on WordPress in plain-text in the database is just… negligent. Frankly, even storing them in the wp-config.php file isn’t the best idea, although better than the database.
WordPress is a very diverse ecosystem… with a lot of very well-developed plugins that do things right… and some plugins that don’t. Security issues DO happen… sometimes even with reputable plugins. If these plugins inadvertently provide Administrator access to the site or open up backdoor access to your database, then your Stripe API keys could be sitting right there for the taking.
Even storage in wp-config isn’t ideal, although much better than database storage in plaintext. But, there are instances where hackers have gotten access to the file system. I’ve seen it before on web hosts with crumby security and I’ve personally seen it more than once on Bluehost back in the day. Any web host that doesn’t properly containerize sites from each other opens up issues. Sites on insecure, shared servers means that a problem on any site on that server can potentially expose the files of any other site on the server. In this case, they could read your wp-config file.
So, storing in plaintext something as potentially dangerous as your Stripe API keys opens up a potential can of worms.
Snicco has a great post (and solution) to this problem here: Solving WordPress’s Pathological Plaintext Problem: Introducing Fortress Vaults&Pillars. I would also like to highlight how this post specifically calls out Fluent Forms for doing it right by encrypting Stripe keys in the database.
You also definitely need to practice responsibility with your own Stripe API keys. Many people don’t because they don’t know any better. Unfortunately, Stripe makes this all too easy because their standard set of API keys is basically like “god mode”. So, it is important that you use best practices when it comes to your Stripe API keys. You can rotate your API keys on some kind of schedule as well as make use of restricted API keys that don’t have the same “god mode” access to everything. You can read Stripe’s documentation about protecting against compromised API keys.
Or…
Just use Stripe Connect. There’s a reason they push it so much – because it IS more secure. And the extremely minor concern that a developer could see your transactions if they cared to (and they really don’t usually care at all) is MUCH more palatable to me than the risk of a bad actor potentially getting my “god mode” API keys to my Stripe account and causing financial damage.
Stripe Versus Others
This entire article and the research I did to write it focuses on Stripe. After all, they’re the most common. Literally every ecommerce site and membership site that I build or manage uses Stripe.
But, Stripe isn’t the only option out there.
Obviously, Paypal is also popular. And my understanding is that OAuth connections to Paypal from developer plugins do NOT expose transactions to developers. It sounds as if Paypal does it right.
There are also other payment gateways such as Mollie, RazorPay, Square, Paddle, etc. They all work differently and have their own methods of connection to your self-hosted WordPress site. Just be aware of the security issues above if you connect by copying/pasting API keys. Inquire with the developer to ensure those API keys are stored in an encrypted manner within the database and not plain-text.
One of the complaints about Stripe for those who have issues is the seeming lack of help. Stripe is a large company and very corporate. While a lot of the info discussed in this article is public, it is buried in corporate documentation that most people don’t read. When you try to get help from Stripe, it can often feel as if they’re peppering you with canned responses. Stripe’s popularity and ease of use for normal people make it so that people will use it without a lot of tech skill. They’re not going to rotate their API keys, for instance, because they barely know what an API key is. When they see that one-click button for Stripe Connect, they may see that notice about the data sharing and think nothing of it. After all, most of us are all too willing to just hit “Agree” on those Terms of Service. 😉
Stripe isn’t the only option, however. You can actually get your own merchant account for your business as well as a gateway such as Authorize.Net. I actually used to do it this way back in the day before Stripe was a major player. When you have your own merchant account, there is a closer relationship there and people to contact for help. Sometimes, you even have your own account rep. It can be a pretty different experience.
With Stripe, you’re more or less using THEIR merchant account. You’re just a user of it. One of multiple millions. So, there’s going to be nothing personal about it.
But, Stripe is easy peasy. And so… we pretty much all use them.
My Own Perspective And Final Thoughts
I will admit… I do this kind of thing all day for a living and I was unaware that usage of Stripe Connect opened up the ability to see my store’s transactions to anybody besides Stripe themselves.
In fact, I was skeptical when I heard it. I thought it was just people being paranoid and it was just a security “conspiracy theory”. When the issue first came across my radar, it seemed as if everybody involved were competitors who may have a vested interest in shedding doubts. The WordPress plugin space is pretty competitive when you dive into it and there’s definitely some cutthroat stuff that happens sometimes behind the scenes. 😉
But, as it turns out, this is indeed the case. Platform account holders on Stripe are able to see certain data going on within connected accounts. And when you connect your store using Stripe Connect, you just became a connected account.
Truth is… this doesn’t personally concern me at all. Truth is, almost every vendor in this business couldn’t care less and never actually looks at this information. Their software sees it and that’s out of necessity so it can work, but the idea that there’s a sea of developers out there sipping coffee and browsing around people’s transactions in their Stripe dashboards is just rather foolish. Most simply don’t care. If Stripe would provide a Connect option that was user-friendly and didn’t expose that information, they’d happily use it. But, unfortunately, Stripe is requiring usage of Stripe Connect without any other options.
So, my opinion is that this is nothing to worry about. You don’t have an expectation of full privacy for your business the moment you start accepting credit cards. That’s just the way it is.
And, if you’re in a business where this small potential risk of exposure of this data to a competitor via Stripe makes your hair curl, then you can look at other options. Perhaps your own merchant account instead of Stripe, or using Stripe Apps directly to process payments (as in, using Stripe’s own payment forms) so there’s no middleman.
The goal here is just that you know about it.
Now that I know about it, I don’t plan to change anything. I still value the digital sovereignty of a self-hosted platform that I own and control. This is why I prefer something like WooCommerce or FluentCart over a SaaS option like SureCart or Shopify. That’s just me and my personal preference. You have to make that decision for yourself.
But, let’s be under no illusions that you have complete privacy. You don’t. In terms of using Stripe, there’s not a lot of difference between using a WordPress plugin and using a SaaS app. The data is still being sent to Stripe… and somebody besides you could see if they wanted to.
Popular Right Now

What If Your Website Was Just… Handled?
I manage WordPress sites for creators and small teams who don’t want to fight tech anymore. Hosting, updates, security, performance — plus a real human you can ask anything.




